Making error-free and effective business decisions
A special program has been developed to minimize the risks associated with the human factor. Training takes place online 🔴
According to the definition of Stanford University, the human factor is the collective influence of employees on the short-term and long-term success of an enterprise.


The self-employed

Consultants

HRDs

Advisors

HRDs

Advisors




The goal of the program
Is to meet the global demand in Western European and US markets for specialists who can counteract and prevent systemic problems associated with the human factor. During the training, interested self-employed individuals and subject matter professionals will be provided with a basic level of the program.
The best graduates will have the opportunity to join the Institute of Information Security team and work in the markets of USA, Germany, Italy and other EU countries.
Each certified participant, thanks to a special program, will receive competitive advantages in the market, which he will be able to monetize on his own many times over.
Who created the program?
The program was created by scientists and experts of the Information Security Institute (ISI) as a response to current challenges in the field of information security of financial institutions. The methodologists included specialists in the field of security, psychology, economics and finance, criminal justice, criminology, information security, as well as specialists in human rights and the human mentality component.

Oleg Maltsev
Scientific leader of ISI Institute, international expert in security industry, creator of SCAD technology, scientist, criminologist, writer, investigative journalist, author of scientific works and monographs on sociology, depth psychology, philosophy and criminology.

Harvey Wolf Kushner
External consultant to the U.S. DHS and the FBI, author of the best-selling Encyclopedia of Terrorism and numerous academic papers and articles, has served as a counterterrorism expert to the DHS Homeland Security Advisory Board, the UN in Austria, and the National Security Bureau in Poland.

Iryna Lopatiuk
Corresponding Member of EUASU. Associate fellow of the Ukraine Academy of Science and the Memory Institute. Analyst, expert in psychodiagnostic and professional selection. She is author, translator, journalist and chief editor of the Newsletter of the Scientific Medical Society—Hippocrates.

Maryna Illiusha
Head of the International Schicksalsanalyse Community Research Institute, adherent of the Venetian school. The main directions of the Institute’s research are the applied aspects of fate analysis—depth psychology, mainly developed by Leopold Szondi, Swiss psychologist, psychiatrist and psychoanalyst.

Olga Panchenko
Expert in criminal, corporate, civil, and intellectual property rights, speaker at the OSCE Human Rights Conference in Warsaw and the “Freedom of Religion and Belief” conference in Rome, member of the Criminology Center research team, editor-in-chief of the Journal of Scientific Results.

Rich Owen
Cybersecurity Leader, Speaker, Author. He has 50+ years of experience, created 5 successful cybersecurity programs, including for NASA. He is a Distinguished Fellow, member of the Honor Roll and past international president of the ISSA. He is the ISC2 recipient of the Lifetime Achievement Award and a member of the Ponemon Institute & Cloud Security Alliance.

Costantino Slobodyanyuk
Presidium Member of EUASU. Associate fellow of the Ukrainian Academy of Sciences. Head of the Strategic council of the Information Security Institute. Head of Сivil Society Organization Kavalyer. Editor-in-chief of the Newspaper Unsolved Crimes. He is engaged in the studies of online reputation management and security of enterprises.

Alisa Novosyolova
Director of the Academy of the Professional Services Industry (APSI). Expert in psychosamology and psychology. Fellow member of the special scientific unit of the Memory Institute—Expeditionary Corps. Presidium Member of the Psychological and Philosophical Scientific Society.
The program consists only of those approaches, tools and methods that have been repeatedly tested in practice in various business sectors over the past nine years and have proven to be extremely effective.
Why was the program created?
For many years, Western security professionals have accepted as an axiom the primacy of technology over the human factor. However, over the past two years, the situation has changed dramatically. Actual practice indicates that without solving the problem of the human factor, technological solutions are not able to provide security.
Today we are at a unique historical point when representatives of the largest consulting companies (McKinsey & Co), the “big four” audit companies (Deloitte, PWC, KPMG, EY), and a number of specialized structures (Merrill Lynch, Information Security Media
Group, Proofpoint, Cyber Security Hub) are forced to admit this fact.
This public consensus was the result of a series of reports that were initiated not only by government agencies, but also by leading cybersecurity organizations, financial institutions, CISOs, as well as analytical and expert companies.
The main conclusion boils down to the need to resolve a key problem in the field of security, namely, the human factor.

Why are human factor experts in demand?
The demand for skills in managing risks associated with the human factor is becoming more acute every day. At the same time, there is a total shortage of trained personnel who are able to comprehensively approach problem solving in the insourcing or outsourcing mode and successfully achieve results.
According to the latest expert reports:
The cause of 95% of security breaches worldwide is the human factor.
WEF report"The Global Risks Report 2022"
82% of registered cyber attacks are related to the human factor.
Proofpoint report "Cybersecurity: The 2022 Board Perspective"
The number of incidents related to insider threats increased by 44%.
Proofpoint report "Cybersecurity: The 2022 Board Perspective"
$4.24 million is the average cost of a data breach.
Ponemon Institute report "2022 COST of Insider Threats"
human factors experts are in demand in companies such as:











How the training happens?
The training program takes place online in small groups of 5 to 7 people
Only suchan approach can provide the necessary level of attention from instructors for each participant and create conditions for the effective transfer of intellectual assets.
In the expert version, the program consists of 10 levels
However, in the basic version, for self-employed persons and specialized specialists, the first two levels will be enough.
During the training program, each participant will be provided with a certain amount of data:
Video materials
PDF presentations
Methodological books (DSP)
Analysis of cases
A package of methods and tools
Practical tasks
Validation tests
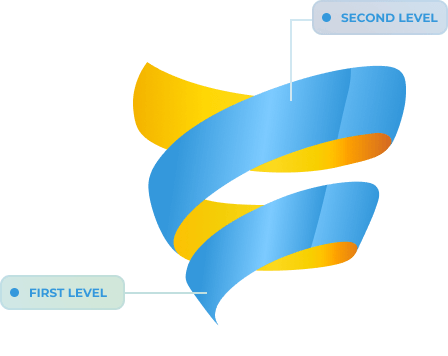
First level
Tasks of the first level of the training program
The central task of the first level is to build an orientation system, a deep understanding of the human factor as an integral system and cause-and-effect relationships, without which it is impossible to analyze business structures or apply certain tools to minimize risks as intended.
At the stage of preparation for the international expert round table “A New Security Paradigm for Financial Institutions”, a group of experts from the USA, Germany, Italy, Great Britain and Ukraine came to a consensus on the approach to working with the human factor.
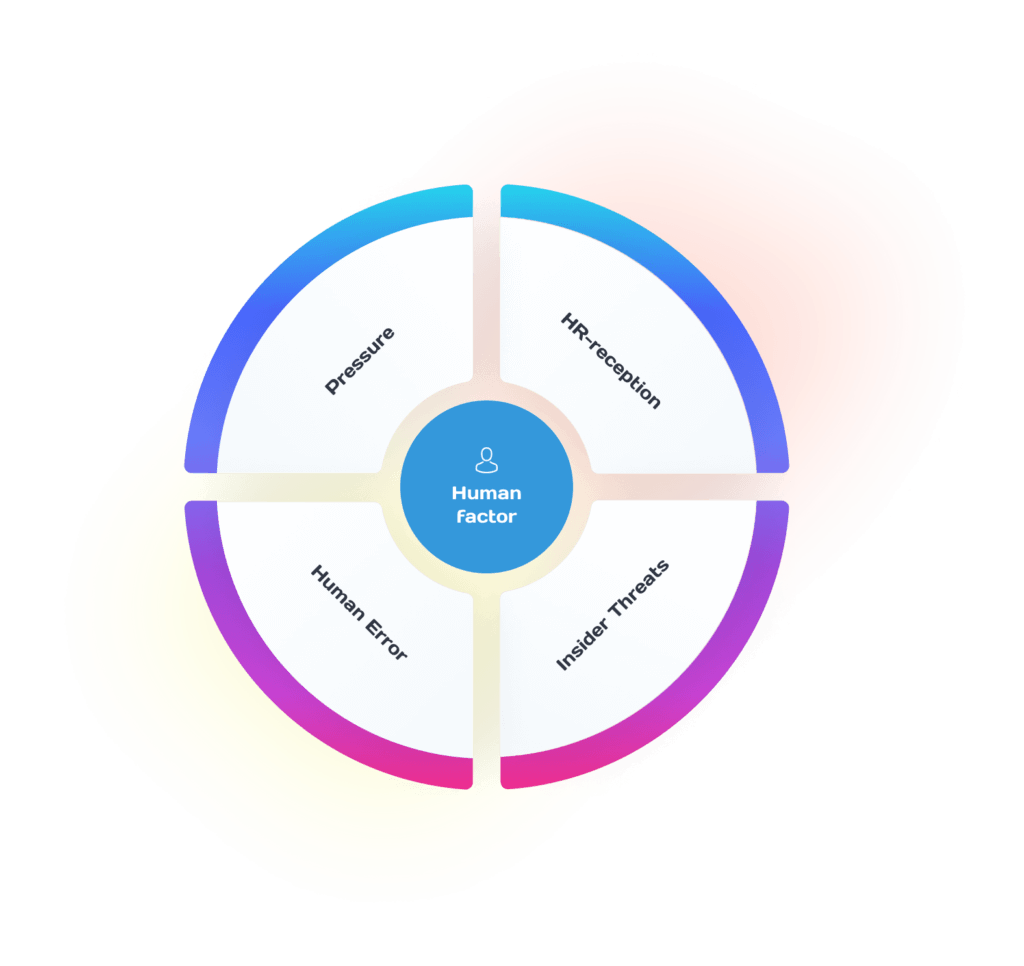
We are dealing with a system consisting of 4 elements that give life to the human factor in any business:
- Employee selection (mistakes made at the professional selection stage);
- Insider threats (insider threats within the company);
- Behavioral stress (mistakes made due to stress);
- Human error (human errors, which experts also call “noise”);
It is with the device and the logic of this system that you will have to get acquainted in detail at the first level of the training program.
Second level
Tasks of the second level of the training program
The key task of the second level of the program is to get acquainted and master the basic tools that will allow you to identify, diagnose and significantly influence the risks associated with the human factor in any business.
- Application of the “alternative of two” method:
- Application of the “frequency” method;
- Application of the method “the mind does not count, but weighs”;
- Application of the “drawing” method;
- Application of the “mind changes” method;
- Application of the “human plays” method;
- Application of the method of movement “after throwing a test rock”;
- Application of the key parameter method;
- Application of the 25-SSBR method in a truncated version;
- The method of conducting the interview;
- The method of conducting surveys and special surveys;
- Signature test.
These are just some of the tools that will be introduced at the second level and, most importantly, integrated into business practice.
Curriculum details
To the astute reader, it is quite obvious that the first two basic levels of the tutorial are parts of one whole system. They are inextricably linked and dependent on each other.
The geometric model of the curriculum at the basic level is a spiral. At the first level, the ecessary logic of the system operation appears in the form of moving in a circle:
All 4 elements are interconnected and directly affect the short and long term success of any company.
At the second level, we spiral up from logic to tools, but we still continue to work with the circle:
By learning to apply tools at the second level, program participants will be able to extract data, cross-check from several points, structure it according to the 4 elements of the circle described above, but most importantly, they will be able to draw certain conclusions, diagnose and identify the most vulnerable elements of the human factor system in business .
Such skills, as we said earlier, guarantee competitive advantages in the market. And the ability to influence the human factor through recommendatory instructions for business based on the results of appropriate diagnostics turns such a specialist into an indispensable and highly paid professional.
The cost of the training program
The demand for skills in managing risks associated with the human factor is becoming more acute every day. At the same time, there is a total shortage of trained personnel who are able to comprehensively approach problem solving in the insourcing or outsourcing mode and successfully achieve results.
As we have already said, these two levels are inextricably linked with each other, therefore the cost is estimated in a similar way – it is impossible to purchase these two levels separately. At the same time, in order to become a participant in the training program at the first level, it is enough to deposit 30% of the total cost – in the amount of $ 600.
After the end of the first level of the program, the participant contributes the remaining 70% – in the amount of $ 1400. After that, the instructors of the institute register the participant at the second level and begin to work according to the standard scheme.
All the above conditions are current as of 04/03/2023
The first steps
30% payment for start
$600
Full program the first level
The first and second steps.
Only one payment
$2000
Why can we teach it?
Thanks to the academic advisor Dr. Oleg Maltsev, The ISI Institute has a unique scientific and research base, as well as the opportunity to test methods in practice in various business structures.
Over the past 3 years, more than 300 cases have been implemented in the field of professional selection
Over the past year alone, the Institute’s specialists have identified more than 50 insider threats in companies in Eastern and Western Europe
Over the past 3 years, the scientific director of the Institute has written more than 15 scientific papers on the topic of the human factor, including closed works such as “Business Sniper” and the “Noise” methodological guide, which are the foundation of this training program
Separate blocks of the program were the subject of a series of scientific meetings and symposiums in Palermo (Sicily), in which experts from the Institute and the “European Academy of Sciences of Ukraine” took part
Over the past 3 years, more than 300 cases have been implemented in the field of professional selection
This is what allowed us to present the model of the program at the closed international round table "A New Security Paradigm for Financial Institutions", which was highly appreciated by experts from the USA, Great Britain, Italy, Germany and Ukraine.
What will you receive at the end of the program?
The program includes a block of skills (soft skills & hard skills) that will be in demand for at least the next 10 years. For advisors, consultants, HDR and self-employed individuals, this is not only an opportunity to gain competitive advantages in the market for solving current problems, but also to minimize the human factor when creating their own projects.
Besides this:
- Status of a certified participant in the ISI program;
- Ability to quickly enter the Western market;
- Access to large checks and corporate clients;
- Expansion of the range of own services;
- Access to the expert community, the Institute's capabilities and consultations for solving non-standard tasks;
- Opportunity to create your own business specializing in solving human factor problems;
- Opportunity to earn in the ISI partner network in new territories of Europe and the USA, including remotely;
- Gaining access to new institute research.
Uniqueness
Most of the existing courses are aimed, at best, at resolving the consequences or one of the 4 elements that collectively give life to the problems of the human factor (Employee selection, Insider threats, Behavioral stress, Human error).
Our program currently has no analogues. This is confirmed by our friends and colleagues who took an active part in the creation of the program: Professor Harvey Wolf Kushner (USA), Andrew Hoskins (Great Britain), Oliver Pahnecke (Germany), Ranieri Razzante (Italy), Vitaly Lunev (Ukraine).
Access to our training program is possible only through the official representatives of our institute or through the official website.

